# Crypto
# crypto1
转字节
MzczZDMyMzg0Yzc4MjQ3NDcyNWMzZTcwMjc0OTRiMjEzMDYzNzAzNTI2NDUyYjY2M2M0MTQ0MzA3YzM3MzQ2MjZmN2Q2NDQxM2YyNDc3NDU2ODIyNGU%3D
去掉末尾
base64 解码
得到
7=28Lx$tr\>p'IK!0cp5&E+f<AD0|74bo}dA?$wEh"N
对照 flag {ISEC-} 发现要么是 + 48 要么 - 48
import string | |
a='''7=28Lx$tr\>p'IK!0cp5&E+f<AD0|74bo}dA?$wEh"N''' | |
b=string.printable | |
for i in range(len(a)): | |
if chr(ord(a[i])+47) in b: | |
print(chr(ord(a[i])+47),end='') | |
else: | |
print(chr(ord(a[i])-47),end='') | |
#flag{ISEC-mAVxzP_4AdUtZ7kps_Mfc3@N5pnSHt9Q} |
# crypto2
rsa 原题
from gmpy2 import * | |
c=0x118dd8ab5df8685c5db5b1242896df41e8e9016f5f16276b6d311b29f0e5f9315530574b51c6e7c82d0c88ab92787d639443b921a452c850db580256ccfd55ee52ea9732821525da1d21351acb230a799ecaa1802c6f24487176c9cae537c3188e083552a84a2aebdd55c4014b41846768d7608970c1e52d9a68e550ef8bb6016adb6f8e0672e1c8198a5442799a5b8142e8d0fadb6e6146a062ef906bd58c46f31bf65263b6142b1976773289dee408ae233b6c0c534dd5092bd7f331c3457971278d335923edc044ba88852680ee39d1cc84a66dc81b70039e2435892b11f310b490c872448f7a8dc718759b2052b0911f758102a59c54dea061a8a3ff6879 | |
n=0x31e22a7a2c5ec946692357dc51014a80530afeb46f419831fcbd896aa1d5cee2d0c69123b3017067afdb3d82b2be3535aebdf11da0fa2b4873233bae6af8a1c2a9344b6f64ade1c6c48a2828130c352053e1729b850774589e8947c8c0a472a8dc90caa542da5cec7f5fa7581747dcb558300437c30b016f769d4a85af8584f311dfb2f9e87fa7d16eaccb0303ecba491619ec7dda72e4037d96c607e666eced582d6eb2c232689fce1c08a54b80cf6d39ef1f2b467d970998c6d54d1779979c89a3b301cd1435bde8787d1141c912cf32b56610fba9205c6e86fefc490c8b2e06f5ed9f775f5b0fe945fa9fca3fc217b4c9dcd4b26676f576d0273b79417b81 | |
e = 65537 | |
for r in range(100000): | |
t1=(1<<1024)-1+r | |
t2,s=iroot(t1**2-4*n,2) | |
if s: | |
p=(t1+t2)//2 | |
q=n//p | |
d=invert(e,(p-1)*(q-1)) | |
print(long_to_bytes(pow(c,d,n))) | |
break | |
#flag{ISEC-OyGdWk_E3gTcPtWUn_OaqD@d76xHyse1} |
# crypto3
简单逆向 爆破 x
from Crypto.Util.number import * | |
a=0xfb9cd6ab42f2be75ae2637794196159de16e49522ed55e83462b0802a0325e1a4e9cbad3 | |
def inverse_right(res, shift, bits=32): | |
tmp = res | |
for i in range(bits // shift): | |
tmp = res ^ tmp >> shift | |
return tmp | |
# right shift with mask inverse | |
def inverse_right_mask(res, shift, mask, bits=32): | |
tmp = res | |
for i in range(bits // shift): | |
tmp = res ^ tmp >> shift & mask | |
return tmp | |
# left shift inverse | |
def inverse_left(res, shift, bits=32): | |
tmp = res | |
for i in range(bits // shift): | |
tmp = res ^ tmp << shift | |
return tmp | |
# left shift with mask inverse | |
def inverse_left_mask(res, shift, mask, bits=32): | |
tmp = res | |
for i in range(bits // shift): | |
tmp = res ^ tmp << shift & mask | |
return tmp | |
def convert(msg,x): | |
msg = msg ^ msg >> x | |
msg = msg ^ msg << 13 & 296229569 | |
msg = msg ^ msg << 20 & 2345273571 | |
msg = msg ^ msg >> 14 | |
return msg | |
def cconver(msg,x): | |
msg=inverse_right(msg,14) | |
msg=inverse_left_mask(msg,20,2345273571) | |
msg=inverse_left_mask(msg,13,296229569) | |
msg=inverse_right(msg,x) | |
return msg | |
def transform(message,x): | |
assert len(message) % 4 == 0 | |
new_message = b'' | |
for i in range(len(message) // 4): | |
block = message[i * 4 : i * 4 +4] | |
#print(block) | |
block =bytes_to_long(block) | |
block = cconver(block,x) | |
block =long_to_bytes(block,4) | |
#print(block) | |
new_message += block | |
return new_message | |
a=long_to_bytes(a) | |
for x in range(2,30): | |
b=transform(a,x) | |
print(b) |
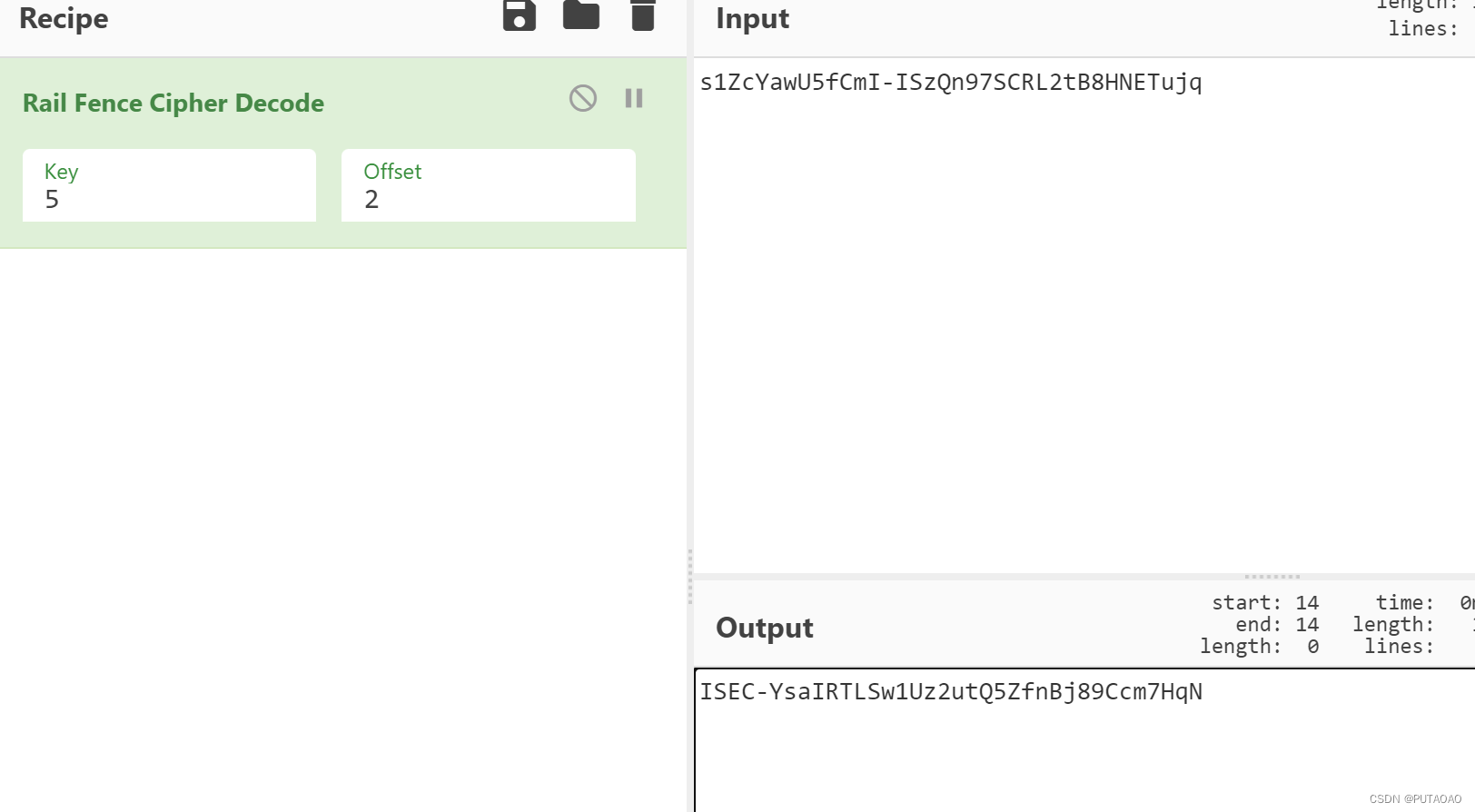
找到有点像 flag s1ZcYawU5fCmI-ISzQn97SCRL2tB8HNETujq
之前还经过什么加密,根据题目名称 Fence,解密