# GipsyT 战队
# 一、战队信息
- 名称:GipsyT
- 排名:28
# 二、解题过程
题目按照顺序填写
# Web
# nisc_学校门户网站
找到登录页面 http://1.14.97.218:28261/home/login/
注册账号
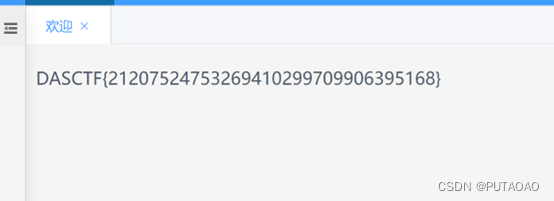
登录得到 flag
# 吃豆人吃豆魂
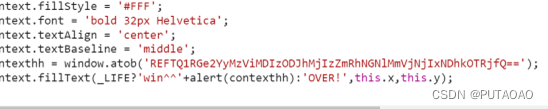
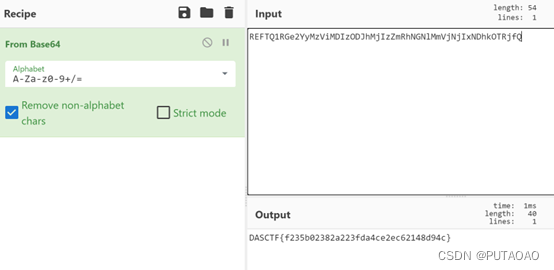
在 index.js 中找到 flagbase 加密之后的
# Crypto
# easystream3
经过 4 次 getrandbits (8) 之后 state 重置了之后是三个 getrandbits 已知
可以爆破出 mask(非预期)有点慢
s=[189, 81, 22, 153, 205, 197, 241, 3, 18, 128, 36, 253, 5, 200, 170, 131, 25, 71, 9, 196, 164, 161, 9, 0, 7, 123, 149, 121, 32, 122, 149, 131, 170, 252, 189, 68, 162, 164, 153, 67] | |
b='DASCTF{' | |
a=[] | |
for i in range(len(b)): | |
a.append(ord(b[i])^s[i]) | |
print(a) | |
c=0b11111001000100000100010111011010 | |
# d=100110011000001110001010 | |
class lfsr(): | |
def __init__(self, seed, mask, length): | |
self.length_mask = 2 ** length - 1 | |
self.mask = mask & self.length_mask | |
self.state = seed & self.length_mask | |
#print(self.state, self.mask) | |
def next(self): | |
next_state = (self.state << 1) & self.length_mask | |
i = self.state & self.mask & self.length_mask | |
output = 0 | |
while i != 0: | |
output ^= (i & 1) | |
i = i >> 1 | |
next_state ^= output | |
self.state = next_state | |
return output | |
def getrandbit(self, nbit): | |
output = 0 | |
for _ in range(nbit): | |
output = (output << 1) ^ self.next() | |
return output | |
for i in range(2**31,2**32): | |
b = lfsr(c, i, 32) | |
if(b.getrandbit(8)==153): | |
if(b.getrandbit(8)==131): | |
if(b.getrandbit(8)==138): | |
print(i) | |
seed=2226048585 | |
f=lfsr(c,seed,32) | |
for i in s: | |
print(chr(f.getrandbit(8)^i),end='') | |
#TF{88ac22ea2ce99c7a325fe6ce2ddd3718} |
# easyrsrsa1
hint:共模攻击
两次 encode 之后得到两个矩阵即可解得原矩阵
比赛时矩阵逆元没想到直接求逆。。
from gmpy2 import * | |
e1 = next_prime(65537) | |
e2 = next_prime(e1) | |
key1= | |
key2= | |
n= | |
def egcd(a, b): | |
if a == 0: | |
return (b, 0, 1) | |
else: | |
g, y, x = egcd(b % a, a) | |
return (g, x - (b // a) * y, y) | |
c1 = matrix(Zmod(n),key1) | |
c2 = matrix(Zmod(n),key2) | |
s = egcd(e1, e2) | |
s1 = s[1] | |
s2 = s[2] | |
if s1 < 0: | |
s1 = - s1 | |
c1 = c1.inverse() | |
elif s2 < 0: | |
s2 = - s2 | |
c2 = c1.inverse() | |
m = power_mod(c1,s1,n)*power_mod(c2,s2,n) | |
flag = [] | |
for i in range(5): | |
for j in range(5): | |
if int(m[i][j])>1000: | |
print(int(m[i][j])-n,end=' ') | |
else:print(m[i][j],end=' ') |
# MISC
# 好怪哦
010 打开发现他是倒的 PK
逆一下
with open("fuck.zip","rb") as f: | |
a=f.read() | |
with open("1.zip","wb") as f1: | |
f1.write(a) |
解压得到 flag.png
发现他缺少头加上 png 头得到文件
改高度得到
